Phishing Report: Fake SMS Texts or "Smishing"
by Jon Lober | NOC Technology
Is that a real text from your boss?
Smishing, vishing, quishing—at some point, the list of phishing attack vectors starts to sound like a bad joke. Unfortunately, these forms of cyberattack are very real—and their results are anything but funny.
SMS Phishing Scams: An Overview of “Smishing”
Smishing is the term that cybersecurity experts use for social engineering scams carried out through SMS texts. The word itself is a portmanteau of “sms” and “phishing.” SMS is the attack vector; phishing is the attack method.
Despite the prevalence and importance of email, SMS (or “short message service”) text is the backbone of global communication. Around the world, more than 23 billion text messages are sent every day. Links sent through SMS have the highest click-through rate of any communication method, between 8.9 %and 14.5%, roughly ten times the average rate of email clicks.
Aware of these remarkable statistics, cybercriminals have proven eager to exploit unsuspecting victims through a wide variety of smishing attacks. IBM reports on several of the most common social engineering techniques used by smishers.
- Financial institution impersonation. Victims receive a fake text from their bank alerting them to a problem with their account. Once the victim clicks the link, they are routed to a fake website that directs them to enter sensitive information like sign-in, payment, or account details, which are then stolen and abused by the scammers behind the attack.
- Customer support impersonation. Very similar to bank impersonation attacks, scammers impersonating customer support from trusted companies send a link to victims asking them to sign-in to their account on a fictitious website or app, where their information is summarily stolen.
- Government impersonation. By abusing the fear of legal mis-steps that many of us quietly carry, scammers impersonate government entities like the IRS or FBI and threaten the application of fines or legal penalties if the victim fails to comply. Once the victim clicks the compromised link, they are often directed to enter personal information—including their social security numbers—that scammers can use to wreak havoc.
- Shipper impersonation. Popular around holidays. Fake texts from Amazon, FedEx, and UPS fill the inboxes of potential victims, prompting them for delivery fees, address corrections, or account updates.
- Wrong number scams. As your own SMS inbox might reveal, these scams are skyrocketing in popularity. “How have you been during this time?” “Hey, how are you?” “I’m Susan and you?” currently populate my own text inbox. Although these may seem amongst the simplest and least nefarious of the smishing attack vectors, in fact they can have some of the most damaging outcomes. These personalized texts can lead to a type of financial attack known as “pig-butchering,” a term derived from the fattening of the victim’s bank account before the fatal blow. The Wall Street Journal’s podcast “The Journal” profiled one such attack in their recent episode “Pig-Butchering: A Texting Scam With a Crypto Twist.”
- MFA / 2FA fraud. Multifactor authentication is one of our simplest, but most effective, tools against modern cybercrime. However, smishers can occasionally outwit unsuspecting victims by pretending to be a friend or family member that is locked out of their account without access to their phone. When the victim sends their “friend’s code” to their “friend” they are actually sending a hacker the MFA code needed to access one of their own accounts.
- Boss or colleague impersonation. Smishing is not confined to a victim’s personal life—it often enters the professional realm as well. Similar to business email compromise (BEC) and gift card scams, smishers will often abuse work relationships in order to achieve their desired ends. Read on to learn about a real attack that smishers recently attempted on one of our own employees.
Our Example: Smishing Attacks at Work
As we have shared before, not even IT support companies are spared from phishing attacks. One of our employees was recently targeted by a smisher impersonating NOC Technology’s CEO.
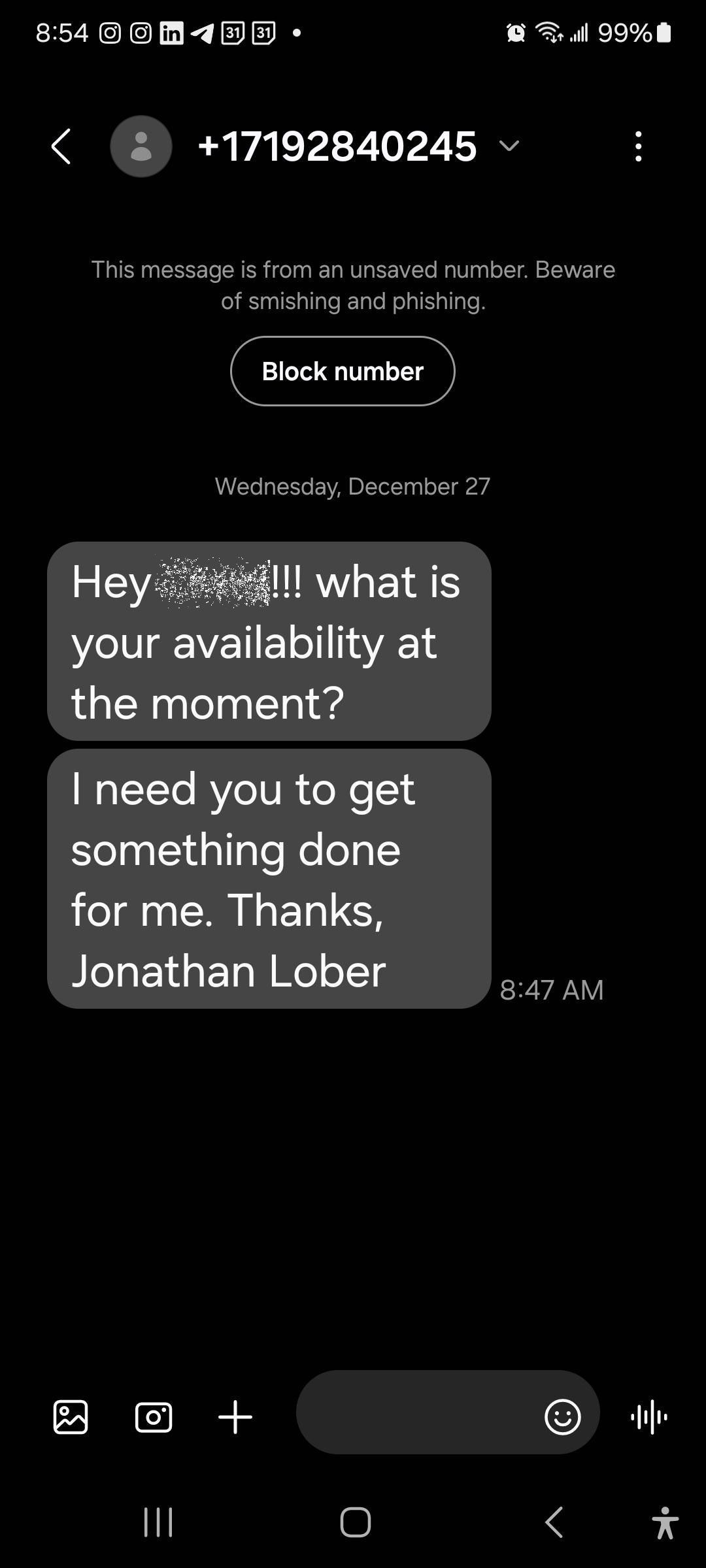
Although simple, this is precisely the type of attack that can easily ruin a career or even sink a small business if not treated with extreme caution.
How does this method achieve its goal?
- Simplicity: It looks like a normal text.
- Authority: Even if the targeted employee would not normally fall for such a scheme, when a boss is involved, they may override normal caution just to make sure that they do not ignore their supervisor.
- Implicit trust of vector: Although many of us have become accustomed to phishing emails, we still often perceive personal-looking SMS texts as potentially legitimate.
- Personalization: The text starts off by directly addressing the recipient by their first name and closes with the full name of the (fake) recipient.
Red Flags: How to recognize this text as a scam.
Although the smishers did a pretty good job, there are still several signs that this text is a scam.
- Unsolicited communication: This is the hallmark of all phishing scams. Always ask yourself, “Was I expecting this?” If the answer is “no,” hit the brakes and calculate the possible risks before proceeding—especially if the sender is requesting something.
- Unknown sender: Identifying a sender as “unknown” can be a bit more complicated than it is with email, since you cannot hover over the sender’s address like you can in email. However, in our specific example, the victim was already personally acquainted with the sender and knew that the unknown number was indeed unknown.
- Warning banner: Most smart phone operating systems now automatically flag unsolicited texts from unknown numbers as a potential threat. Do not ignore such warnings.
- Mix of personal and formal conventions: This is where the smisher overcooked their scam a bit. Most people do not start their text off with “Hey _____!!!” and end it with their full name. Unless the purported sender is communicating cross-culturally, unusual combinations of social conventions should always sound an alarm.
What to do if you encounter a fake text.
Once you have identified a fake SMS text, take the following steps.
- Do not respond in any way. Resist the urge to take vigilante justice by messing with the sender. Your response will simply indicate to the scammer that they have hit on a legitimate phone number that they can sell to another cybercriminal or attempt to compromise in a future attack.
- Block the number. Most operating systems offer you the opportunity to block the sender directly from the text screen. Block the number immediately.
- Delete the text. Eliminate the text from your inbox to prevent a future accidental reply should you happen to forget why you did not take action originally.




