Phishing Report: Geek Squad Scam
by Jon Lober | NOC Technology
NOC Technology takes a look at the popular Geek Squad Email Scam: How to identify it, how you should respond, and what to do if you fell for it.

We continue our series on phishing scams that are currently making the rounds. This week, we will take a look at another phishing email received by one of our staff members in their personal accounts. A quick internet search reveals that this Geek Squad email invoice scam has one has been making the rounds for at least a year—and probably much longer.
So, what did the scam look like, how did our staff member catch it, what should you do if you receive it, and what should you do if you fell for it?
Read on.
If you need a refresher on what phishing is and why it matters, you can read our introductory article on phishing before you continue.
Overview: Geek Squad / Best Buy Phishing Email Scam
In general, this is a very simple “wide-net” phishing scam. It uses basic phishing methods in order to allow for the widest possible set of potential targets. By doing so, the scammer hoped to ensnare a few victims by a shotgun approach instead of a precision attack.
Here are the specifics.
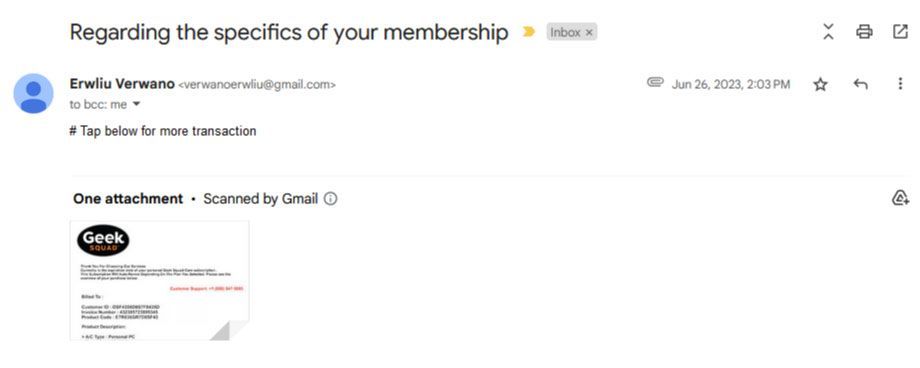
In June 2023, our staff member received an email in his personal Gmail inbox titled “Regarding the specifics of your membership” from “Erwliu Verwano.” An invoice with the file name “Membership Purchased #450968409457.jpg” was attached to the email and prominently featured the Geek Squad logo.

The invoice was for a Geek Squad subscription for protection of a personal Windows computer had been auto-renewed for a total of $419. The invoice notified the staff member that the auto-renew would be charged to his account unless he called the number listed in the invoice within the next 24 hours.
If our staff member would have called, the scammer would have likely picked up the phone and done one of the following:
- Requested personal information to verify the account
- Requested username and password information
- Requested financial information to look up the payment type associated with the account
- Requested remote access to the user’s computer to verify the type of computer
The scammer would have then used any information or access provided to install malware or illicitly access the victim’s accounts. The scammer could then make fraudulent purchases, steal directly from victim’s bank accounts, or infiltrate the victim’s network to identify and attack additional victims.
Phishing Lures: The Geek Squad Phisher’s Methods
This is a pretty sloppy scam, yet a few of the methods that the phisher used could be enough to trick some users.
- Simplicity: Though it might make some people think that the email is a scam, to others the very lack of information in the email might make it feel legitimate. Less information in the email means fewer triggers for wary victims.
- Attached Invoice: The subtle detail of attaching an invoice used a veil of legitimacy to mask the scammers intentions. Since the attachment did not contain any malware, Google’s automated scan indicated that the file was safe to open, adding an additional layer of apparent legitimacy.
- Name and logo well-known companies: The Geek Squad and Best Buy names are synonymous with security and reliability. The scammer’s use of these names and logos played directly to the potential victim’s inherent trust in these companies.
- Invoice Details: The scammer included an overwhelming amount of specific information in the invoice. Customer IDs, Invoice Numbers, Product Codes, Charges, Dates, and Devices all conspired to make the invoice seem legitimate in today’s automated market environment.
- Passive call to action: The invoice did not directly ask the victim to do anything, so it did not trigger the internal alarms that (should) go off when you receive a pushy email asking for payment. This is perhaps the most sophisticated technique used by the phisher.
Red Flags: How to recognize the Geek Squad Scam
Although the phisher has put some effort into their attempt, this particular email is riddled with errors that should raise red flags for potential victims right out of the gate. Anyone with even rudimentary awareness should be suspicious from the very beginning.
- Communication regarding an unsolicited service: In this case, the intended victim knew that he had never purchased services from the Geek Squad, nor noticed any such billing on his bank or credit card statements. Though scammers may try to scare you into thinking that someone else used your card to purchase such a service, your bank account will not lie.
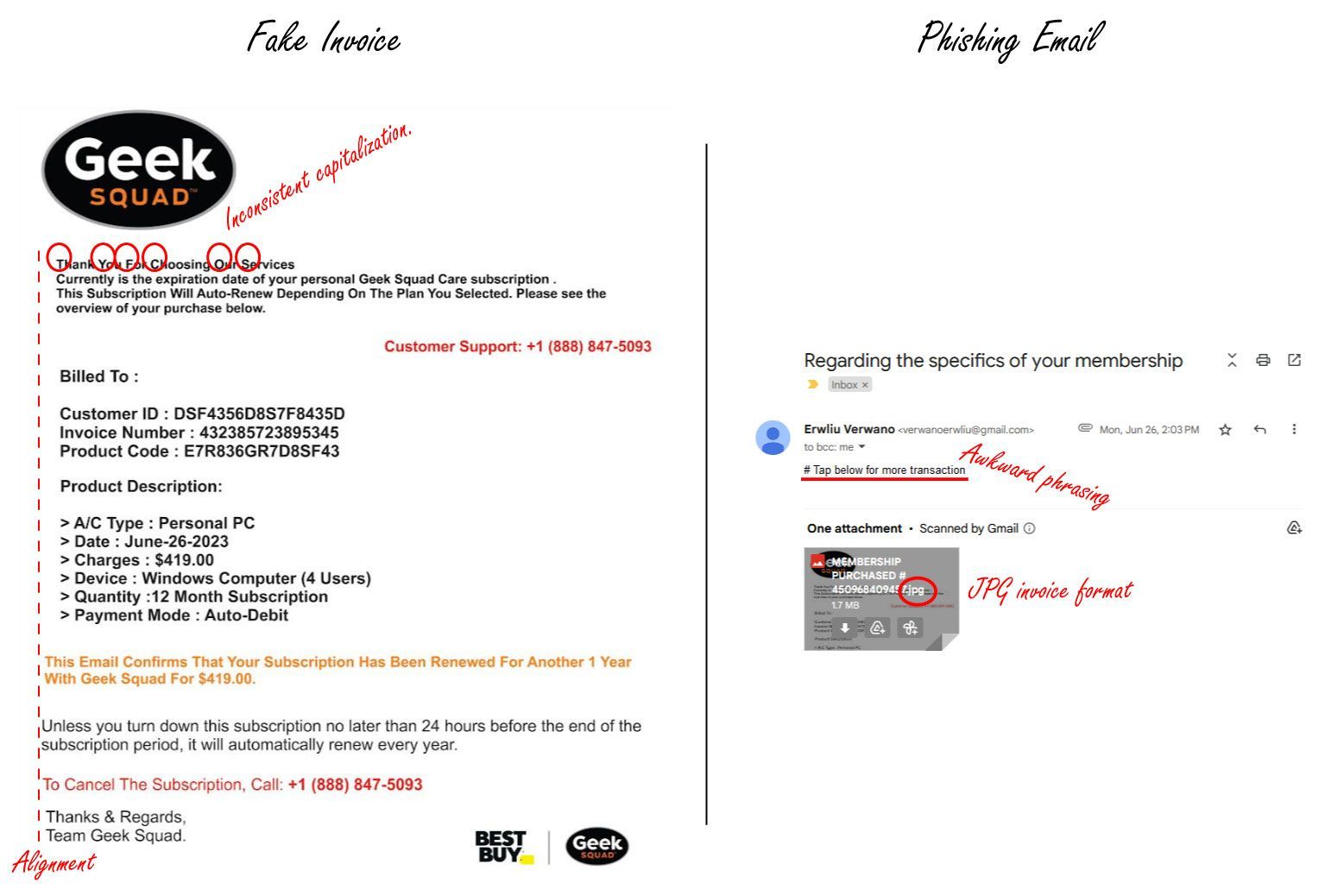
- Email sender: Many scammers conceal their identity by spoofing their sender name. In this example, the email would have appeared to have been sent by someone like “Geek Squad Billing Team.” In our case, Erwliu did not even try. Incorrect grammar: A corporate giant like Best Buy has access to competent writers, editors, and basic spell check. Grammatical errors, awkward phrases, and a willy-nilly approach to capitalization all scream “SCAM.”
- Unprofessional layout, design, and language: Although this shame invoice is not as bad as others we have seen, close observation reveals that the left margin is not aligned, and the opening paragraph of the invoice is a smaller font size.
- No personally identifying information: Everything about this email is generic. It is Bcc’d to an anonymous list of potential victims. As a result, the scammer did not include any specific information in the invoice or email—such as the potential victim’s name, address, or email. A more professional attacker could easily include these basic details, but in this unsophisticated case, the phisher did not do so.
- JPG Invoice File Format: No legitimate company will send a digital invoice in JPG format. JPG is an image file format and is not intended for documents. Most legitimate invoices will be in PDF format—though even those can be scammed. If you see an attached invoice in JPG, PNG or other image format, the email is almost certainly a scam.
What to do when you encounter the Geek Squad phishing email.
Combined, these red flags are enough evidence for a recipient to firmly conclude that this email is not legitimate. Our staff member quickly recognized the signs of phishing email, and the phisher ended up with any empty net.
However, many people still fall for such attacks. People at higher risk for falling for this attack includes people with:
- limited exposure to phishing attempts
- no cybersecurity awareness training
- a legitimate purchase history with the spoofed company—Geek Squad or Best Buy in this case.
Attempts are currently common and often painfully effective. In October 2022, the FTC (Federal Trade Commission) issued an alert to consumers about Geek Squad-related phishing. The FTC asks users to report any fraud and their website makes it simple to do so. Best Buy also requests that you report such emails to them for investigation by calling them at 1-888-237-8289.
Finally, once you have reported the scam. Report the email as phishing to your email service provider.
To summarize, if you encounter such communication:
- Never click any links.
- Report the email to the relevant parties.
- Report the email as phishing to your email provider.
- Block the sender.
- Permanently delete the email.
Did you bite? What to do if you fell for the Geek Squad phishing scam.
Uh-oh. You took the bait. You clicked. You called. Now what?
If you paid a scammer through Western Union, MoneyGram, or a debit, credit, or gift card, you should immediately contact the financial institution that facilitated the payment and let them know that it was a fraudulent charge and ask them to reverse the payment or refund your money. If you sent cash through the USPS, you can attempt to intercept your package before the scammer receives it. If they receive the cash, or if you paid in cryptocurrency, you will probably not be able to recover your money.
If a scammer has access to your personal information such as your social security number or financial information, visit identitytheft.gov to report the theft and put together a plan to recover your identity.
If you gave a scammer your username and password, or suspect that they have remote access to your phone or computer, you should run antimalware software on your computer immediately and seek professional help from a cybersecurity expert.
The FTC maintains a helpful page of advice and resources for anyone that has fallen prey to a phishing scam and provides specific instructions for what to do in your particular dilemma. In many cases, you will have a better outcome if you can respond as quickly as possible to the issue. Act quickly and seek professional assistance if you feel that the issue is beyond your ability to address.




